Your Trusted Source for Insights, Innovation, and Expertise
Our content offers you the knowledge and tools to stay ahead in a rapidly evolving industry.
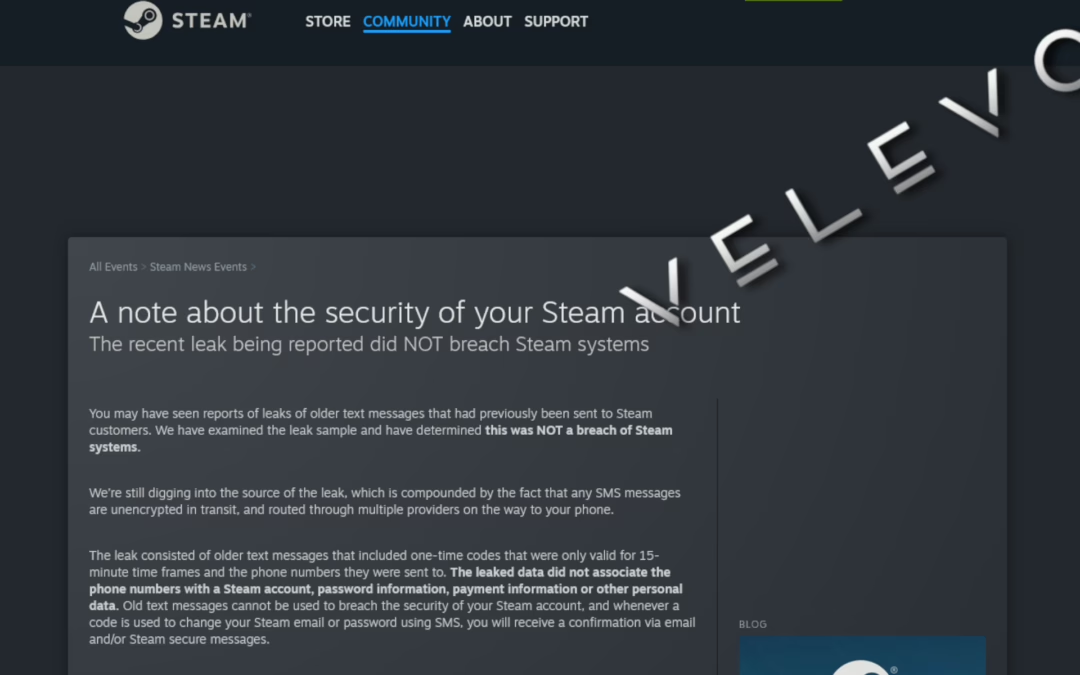
Steam Leak 2025: What Really Happened & How to Protect Your Account Now
Valve’s Statement in Detail: No Need to Panic, But Stay AlertYesterday, the term "Steam Leak" was trending, but what actually happened?Valve has issued a clear statement, and there’s good news: 🔹 What did NOT happen: No access to Steam accounts, passwords, or payment...

Beware of Crypto Traps! These Scammers Are Lurking Online!
Beware of Crypto Traps! Scammers Lurking Online! In the world of cryptocurrencies, there are not only opportunities but also numerous dangers. As IT forensics experts at VELEVO®, we help you understand these risks and protect yourself against crypto scams. In this...
Beware of Crypto Traps! These Scammers Are Lurking Online!
Beware of Crypto Traps! Scammers Lurking Online! In the world of cryptocurrencies, there are not only opportunities but also numerous dangers. As IT forensics experts at VELEVO®, we help you understand these risks and protect yourself against crypto scams. In this...
CES 2025: VELEVO.NET Pioneering AI Innovation with NVIDIA Systems
VELEVO.net: Pioneering AI Innovation with NVIDIA Systems At VELEVO, we’re passionate about creating extraordinary experiences through cutting-edge technology. As a proud host of NVIDIA systems, including the highly anticipated AI servers, we’re thrilled to share...
Latest News
DSL Shutdown 2025: Federal Network Agency Plans & Your Next Steps
DSL Shutdown: How to Prepare for the Fiber Optic Transition What You Need to Know and How to Act Now Searches for “DSL shutdown Federal Network Agency” are skyrocketing. Time to break down the facts: What’s the plan? Will you need to cancel your DSL contract soon?...
Beware of Crypto Traps! These Scammers Are Lurking Online!
Beware of Crypto Traps! Scammers Lurking Online! In the world of cryptocurrencies, there are not only opportunities but also numerous dangers. As IT forensics experts at VELEVO®, we help you understand these risks and protect yourself against crypto scams. In this...
CES 2025: VELEVO.NET Pioneering AI Innovation with NVIDIA Systems
VELEVO.net: Pioneering AI Innovation with NVIDIA Systems At VELEVO, we’re passionate about creating extraordinary experiences through cutting-edge technology. As a proud host of NVIDIA systems, including the highly anticipated AI servers, we’re thrilled to share...
Kaspersky removed from the Play Store – What does this mean for you and your company?
Hello dear readers, If you use an Android device and have chosen Kaspersky as your preferred security app, you may have noticed that Kaspersky products are no longer available in the Google Play Store. As an IT system house, we want to inform you about this important...









